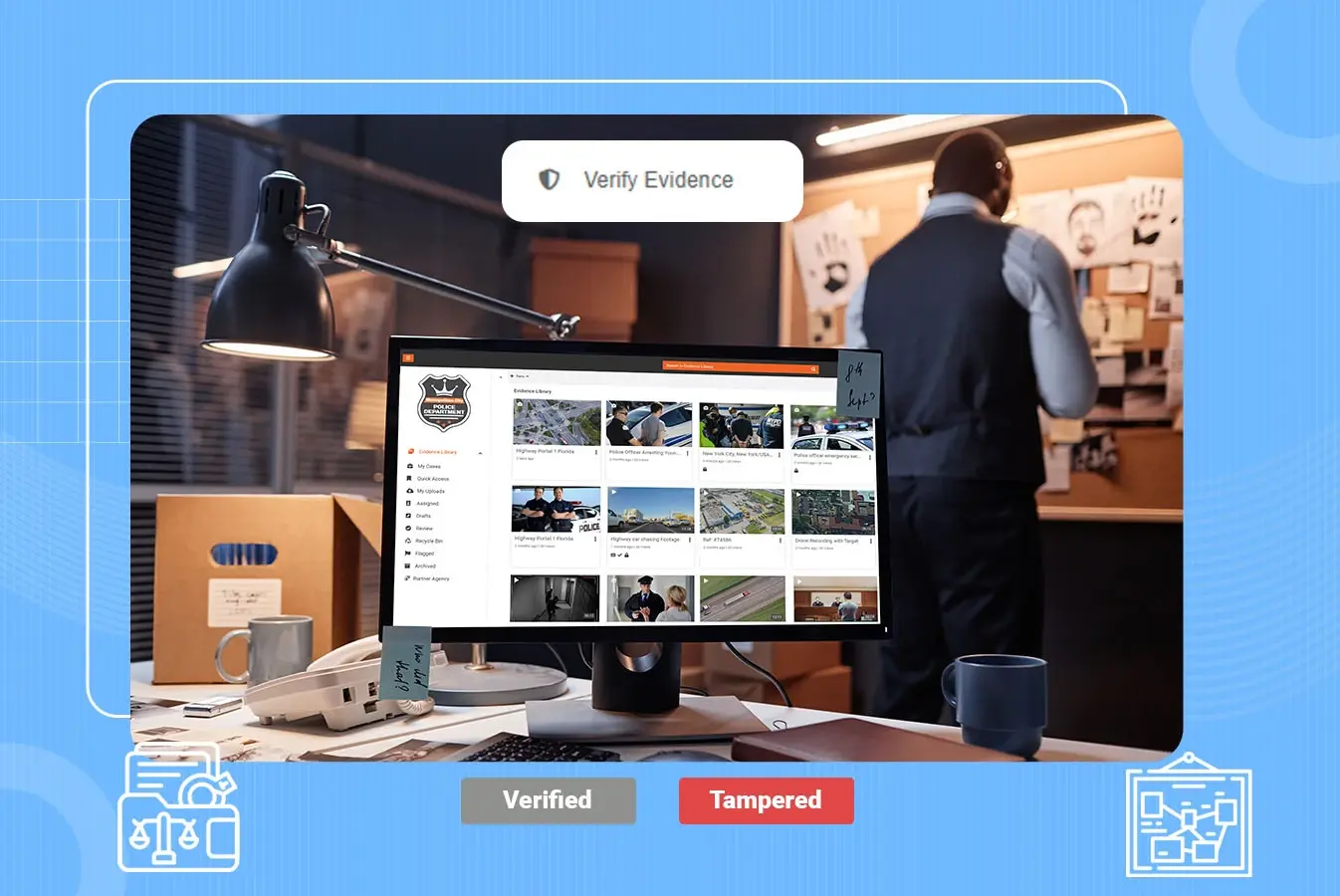
Evidence, digital and otherwise, is subject to spoliation due to multiple intentional and unintentional factors.
However, before we dive into the debate of preventing spoliation of evidence, we need to understand what is spoliation, in what conditions evidence is considered spoliated and then move to see what a proper solution to the issue at hand can be.
That is why we’re here with this blog, to tell you all that and more.
What Is Spoliation?
Spoliation is the tampering, suppression or destruction of evidence, or any similar act that renders the evidence as invalid for prosecution and case hearings.
The act may be done intentionally or unintentionally, and variable charges may be held against the party responsible, such as the custodian of evidence or the entity who held possession of the evidence when it was spoliated.

In terms of digital evidence, this could mean tampering with electronically stored information (ESI) that is stored as evidence on a system.
The evidence could be tampered with to change the contents of the file or erase the evidence entirely. Either way, this renders the evidence utterly useless and invalid.
Spoliation is punishable by law in several countries of the world, including the US, with the individual(s) responsible for spoliation to be charged with fines and/or incarceration. The Federal Rule of Civil Procedure 37 (e), amended in 2015, indicates how the court is to act under law if a party fails to preserve evidence.
When Do We Consider Evidence to Be Spoliated?

There are a few prerequisites about evidence for it to be considered spoliated if tampered with or damaged. For instance, evidence is recorded from the state it was obtained. According to the Washington Court of Appeals, spoliation is not considered until a lawsuit is filed.
Any changes made to said source of evidence prior to the lawsuit is not considered as spoliation of evidence. This is because the object of interest, that may later provide evidence, prior to the lawsuit would be a simple object of day-to-day use.
A well-known instance of spoliation of evidence is the case of Cook v. Tarbert Logging, Inc., where Raymond and Arlene Cook complained about a collision of their truck in February 2009, with a truck driven by an employee of Tarbert Logging Inc. However, a lawsuit was filed two years after the incident, and in the meantime, Cook’s truck was salvaged and sold for parts.
Digital evidence too would not be considered spoliated if any changes were made to it prior ingestion.
However, if spoliation is suspected, law enforcers need to implement techniques to determine if the evidence in question has been spoliated. Moreover, prevention of unintentional spoliation of evidence data is also a necessary measure to take.
How Can We Determine and Deter Spoliation?

With the importance of evidence integrity considered, the initial step should be to prevent data breaches in all forms to avoid accidental and intentional spoliation of evidence.
The first and foremost measure to be taken would be enhanced security for the files stored on the digital system. The evidence needs to be protected, not only while in storage, but also when in transit during sharing or downloading.
Threats can be internal too, and individuals authorized to access a system and the files within can also be a cause of the spoliation of evidence. Systems that hold digital evidence should be able to limit access in terms of user roles and allow to limit access to files individually.
If spoliation does not involve complete destruction of evidence data, then the evidence files can only be rendered invalid through tampering of the contents it holds. If evidence is tampered with and not detected, it could affect the outcomes of a court proceeding or hearing.
Implementing techniques for tamper detection, such as a cryptographic hash algorithm, can allow us to detect and thus, prevent any tampering with digital evidence files. These files can be restored to a previous non-affected version of the same if a version history is implemented.
A complete audit trail of the system would also assist in keeping track of activities performed by individuals registered to use the system upon the files stored, thus deterring any possibility of spoliation via internal resources.
Individual file-based logs can also be maintained through a complete chain of custody, which monitors if any individual, internal and external alike, would make changes to the files, by deleting or modifying the contents.
VIDIZMO DEMS – How It Provides an Optimal Solution for the Problem Presented
VIDIZMO Digital Evidence Management System is an IDC MarketScape 2020 recognized digital content management solution that can serve to be a viable option for your concerns regarding evidence spoliation. The system is designed to cater to everything evidence – from ingestion, to storage, security, accessibility and sharing.
When it comes to security, VIDIZMO is a secure video hosting platform that offers encryption with AES-256 to protect all files stored on the system. AES-256 is one of the best encryption ciphers that technology today has to offer, hence ensuring no breaches are made into the system which could result in tampering and spoliation of any sort. VIDIZMO also offers optional DRM support and allows you to choose between AES or DRM for video encryption.
To ensure evidence stored on the system is kept intact and even authorized personnel cannot, in any way alter the contents of the evidence files, VIDIZMO allows for users to be segregated into user groups, each having separate permissions.
Separate portals can also be created to limit access and segregate based on departmental divisions and other factors.
For further security, individual files can be given access restrictions in VIDIZMO DEMS to allow specified users or user groups to be able to access them. File sharing can also be restricted or limited to view only or other specifications, cutting down the probability of accidental spoliation to nearly zero.
VIDIZMO DEMS also utilizes SHA3-256 hash function for tamper detection of stored evidence files. Evidence is marked tampered if said hash function number deviates from what was attributed to the original file.
While this is highly unlikely to occur in our system incorporating top-notch security measures to maintain evidence integrity, the presence of the feature ensures to you that the evidence file you are dealing with has not been tampered with in any way.
Another element that VIDIZMO incorporates is the provision of an audit log of all activities performed by each individual user on the system, in their chronological order. The events are recorded with track of their date and time of incident, the IP address used to access the system, as well as certain other details.
Besides an audit log of the system, VIDIZMO also offers you a complete chain of custody for each individual evidence file. This keeps a record of all the workflows involving a certain file, who accessed it, and other processes regarding it.
But VIDIZMO DEMS was not designed to simply be a spoliation deterrent. The tool itself is a complete digital evidence management solution, designed with plenty of other dedicated features than the ones we have already discussed.
For further details on each of these features, be sure to check out our DEMS feature page.
You can also talk to a VIDIZMO DEMS expert.
You can also get VIDIZMO DEMS for yourself and test out each of the features firsthand using our free trial.
Posted by Muhammad Nabeel Ali
Nabeel is an Associate Product Marketing Manager at VIDIZMO and an expert in evidence management technologies. He is actively researching on innovative trends in this domain such as Artificial Intelligence. For any queries, feel free to reach out to websales@vidizmo.com